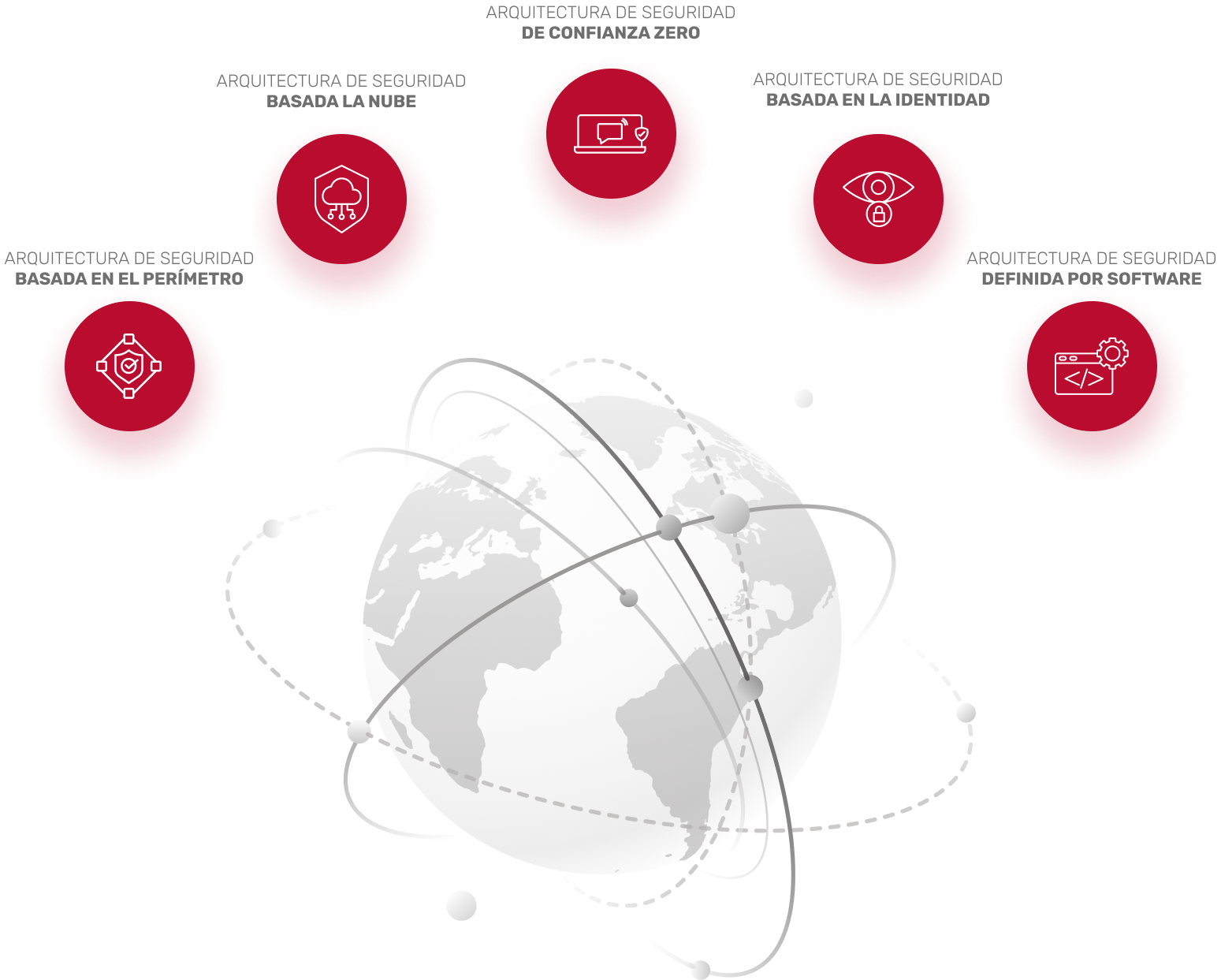
We build a cybersecurity architecture to ensure that all components of your IT assets are protected, including cloud, networks, IoT, endpoints, and mobile.
This architecture includes Zero Trust security models for devices, users, data, networks, workloads, automation and harmonization, visibility, and analytics to ensure the protection of your data and IT resources wherever they exist.